Description of the Exercise
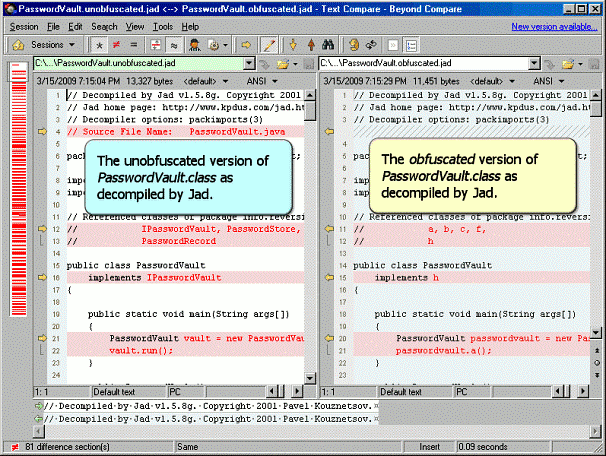
Use Java bytecode anti-reversing tools such as ProGuard, SandMark, and CafeBabe on the Java version of the Password Vault application to apply the anti-reversing techniques Eliminating Symbolic Information and Obfuscating the Program with the goal of making it more difficult to disable the trial limitation. Instead of attempting to implement a custom control flow obfuscation to inhibit static and dynamic analysis as was done in the solution to the Wintel Machine Code Anti-Reversing Exercise, apply one or more of the control flow obfuscations available in SandMark and observe its impact by decompiling the obfuscated bytecode using Jad. Show that the solution to the Java Bytecode Reversing and Patching Exercise can no longer be carried out as demonstrated.
Software for the Exercise
Password Vault Java Trial Application
ProGuard (java bytecode obfuscator)
RetroGuard (java bytecode obfuscator)
SandMark (java bytecode obfuscator)
CafeBabe (java bytecode editor)
Solution for the Exercise
For instructional purposes, an animated solution that demonstrates using anti-reversing tools to protect the Java Password Vault application from being reverse-engineered was create. The tutorial begins with the Java Password Vault application, ProGuard, SandMark, Jad, CafeBabe, and a Java JDK installed on Windows®. Note: viewing the animation requires a Flash player, such as Ruffle.
Java Bytecode Anti-Reversing Exercise