Description of the Exercise
Using the Windows Sysinternals suite of diagnostic tools, identify the behaviors of the Alarm Clock application that make it a software Trojan. Note any filesystem, memory, registry, or other activity that is unrelated to the program’s advertised functionality. Note that even though the Alarm Clock application is written in Java, the bytecode has been agressively obfuscated to discourage the use of decompilation as a strategy for learning the application’s behavior.
Software for the Exercise
Alarm Clock Java Windows® Application (obfuscated bytecode)
Alarm Clock Java Source (unobfuscated)
Sysinternals Suite (system monitoring and debugging suite)
Solution to the Exercise
The Alarm Clock application is a benign software Trojan that in addition to being a rudimentary alarm clock, collects information about the Windows® installation, and randomly scans for computers on the Internet or Intranet that will respond to an ICMP ping. The application logs all of the information it gathers into several files in a directory off of the root file system, or off of the current directory (if the root files system is not writeable). The specific information gathered by the application is as follows:
- Registry data on the Windows® installation including the license “key”.
- Registry data on the currently installed programs.
- The locations of office, pdf, and general text documents.
- IP addresses of random Internet/Intranet hosts that respond to an ICMP ping.
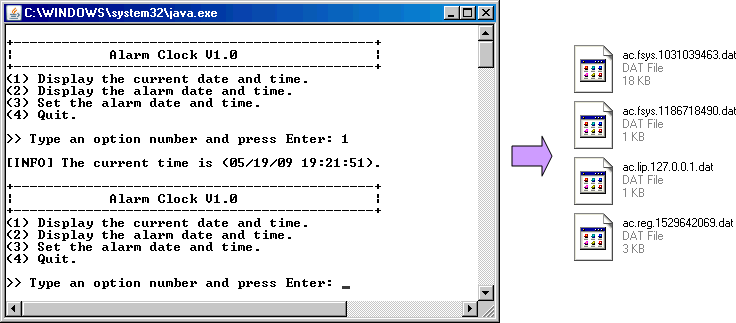
Figure 1. Malware Identification and Monitoring Exercise Solution